SSL Inspection
Manage and control SSL-encrypted Web traffic – just as you do non-encrypted traffic.
About CyBlock’s SSL Inspection (SSL-I) Feature. SSL-I counters the security risks inherent in SSL encryption while preserving its benefits. So what is SSL-I? It’s a customer-configurable, security enhancement feature in our CyBlock Appliance and CyBlock Software products. When in use, SSL-I enables these products to categorize encrypted (HTTPS) employee Web requests – just as they do those that are not encrypted. This in turn enables CyBlock customers to better identify and defeat malware and other types of security threats. SSL-I also enables customers to get a clearer and more complete picture of the type, volume, and origins of all encrypted Web traffic in their network.
Using Custom Categories. As with other policy setups (filtering, bandwidth management, etc.), custom categories can be very useful in implementing a finely-tuned, precisely targeted SSL-I routine. For example, a custom category can be created to see that some of the encrypted URLs in a particular category are inspected. In this case, the customer creates a custom category and enters those particular URLs. The customer can create another custom category to ensure inspection of local-interest URLs that are not in our URL List. Another can be created to exempt from inspection some of the encrypted URLs in a particular category.
Note: Traffic that is exempt from inspection is said to be “tunneled.”
The Overall Process. When SSL-I is enabled, encrypted Web requests that are not permissible per the customer’s usage policy will be immediately blocked. Conversely, those that are permissible will be promptly forwarded to the Web. CyBlock logs these actions so that the information can be used in real-time displays and after-the-fact reports to management and IT.
Customer Control. Customers can configure CyBlock Appliance and CyBlock Software to:
- Inspect no encrypted traffic.
- Inspect all encrypted traffic.
- Inspect certain types of traffic.
Of these three choices, the last (i.e., “some”) is the most flexible and powerful. It enables customers to configure the product to:
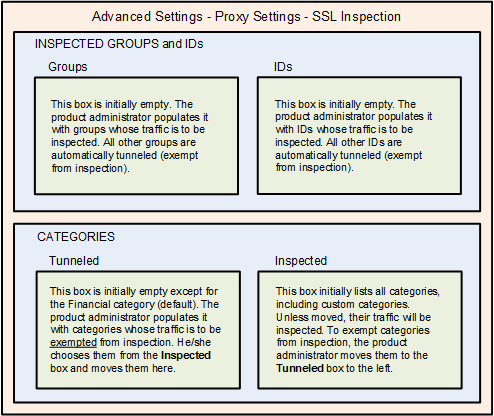
- Inspect traffic in certain categories (including both standard and custom categories).
- Inspect traffic initiated by certain groups or users.
SSL Inspection Setup Screen. The illustration below depicts the straightforward setup screen that customers use to configure the SSL-I feature to meet their own particular needs.
Benefits to the Customer. SSL-I enables customers to take advantage of the positive aspects of SSL encryption, such as information privacy protection, while countering the negative potential, e.g., hidden malware.
Like to Learn More? To learn more about SSL encryption and CyBlock’s SSL-I feature, see our SSL Inspection Tech Brief.
© Copyright 1996-2024 Wavecrest Computing. All Rights Reserved.Thank you Wavecrest!"
-Chris Warren The Five Star Institute







