

Create easy-to-understand, detailed reports to share with stakeholders.
Managers Only See Actual User Web Browsing
- Create custom reports that provide management with exactly what they need.
- Accurately identify actual user clicks, providing managers with clear, useful data.
- Reduce the volume of information by showing managers only relevant data.
- True team collaboration is now possible with pertinent reports for all stakeholders.
- E-mail, print, share detailed reports via HTML, PDF and CSV formats.
Extensive Library of Prebuilt Reports
- Extensive library of prebuilt reports in user-friendly formats for complex data.
- Empowers you to start using impactful reports instantly, with minimal effort required.
- Distribute ready-to-use reports manually or schedule for automatic delivery.
- Report templates can be restricted to only the manager's defined group(s).
- Share reports in multiple formats, including HTML, PDF, and CSV.
Sample Selection from Report Library

Productivity & Time Online
Managing Productivity & Session Time Online
- Application and Website reports with session duration.
- Monitoring productivity and usage of company web services.
- Easily see how much time users are spending online.
- See session time by friendly Website name, not by ambiguous Domain Name.
- Accurately identify actual user clicks, providing managers with clear, useful data.
User Behavior Analytics
- Harness the power of Cyfin to decode complex firewall network logs.
- Advanced algorithm converts technical data into clear human actions.
- Get clear web activity reports, simplifying understanding and action.
- Analyzes large volumes of data over long periods of time.
- Grasp employee web usage for a more efficient, secure online environment.
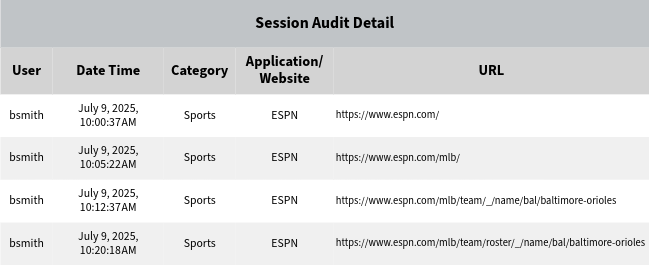
Smart Engine Session Audit Analysis
Recognizable Name, not Ambiguous Domain Name.
Recognizable Name, not Ambiguous Domain Name.
- Unique feature that converts unclear domain activity into friendly site names.
- Today’s complex Websites utilize many different domains just to load a single page.
- Firewall reports view distinct domains as unique, even if they serve the same site.
- Managers want session duration by site name, not by ambiguous Domain Name.
Most Popular Integrations
Additional Features & Exceptional Support: Quick Overview
- Seamlessly integrates with AD for secure, efficient management.
- Supports all Syslog-enabled firewalls, no third-party server needed.
- Supports various data sources: syslog, log formats, databases, and REST API.
- U.S.-based expert technical support team.
- In-depth product knowledge for superior assistance.
- Committed to your success with comprehensive trial support.
Choose the Right Cyfin Deployment
Virtual - Container Deployments
Benefit from highly scalable and easy-to-expand VM resources, with comprehensive support for VMware, Microsoft Hyper-V, and container environments, including Docker.
Deploy effortlessly with our VMware OVA VM Template for quick integration into any VMware system, or use our Windows Hyper-V Installer for a seamless installation experience. Embrace the convenience of a tailored deployment that fits your infrastructure needs with Cyfin's virtual machine and container deployment options.
Wavecrest Cloud Platform Deployment
Experience the convenience and security of Cyfin's cloud deployment. Deploy in minutes with simple, intuitive steps, without the need for additional hardware or software, and no ongoing maintenance costs.
Rest assured with our state-of-the-art SSAE 18, SOC 3, SOC 2 certified data center, and HIPAA and HITECH audited infrastructure Embrace the ease and reliability of cloud-based web monitoring and reporting with Cyfin.
How does it all work?

Set Up Real-Time Import
Directly Syslog to Cyfin, no third party software delays.

Smart Engine Processing
Proprietary machine-learning algorithms that converts raw firewall connection data to actual Web browsing.

Set Up Visualizer & Report Delivery
Easily visualize your data by setting up custom dashboards. Most flexible scheduling & delivery options - HTML, PDF and CSV formats.

Automate & Collaborate
Getting the right information to the right people, in the right format, at the right time.
Get Started with Cyfin: Request Info, Pricing, Demo, or Trial
Thank you for your request!
We’ll reach out within one business day to address your needs, whether it’s exploring pricing, answering questions, scheduling a personalized Cyfin demo, or starting your free trial.
What our customers are saying about Cyfin:
"We just completed a rigorous evaluation of Wavecrest Computing's Web-access reporting product, Cyfin Reporter. We found that Cyfin produces comprehensive information that can help managers quickly correct inappropriate or ineffective surfing. When this is done, they should see significant cost savings in the areas of work force productivity, legal liability reduction, and network bandwidth conservation. In addition to these functional benefits, we found Cyfin to be highly scalable, interoperable with a wide variety of servers, firewalls, and operating systems, and definitely user-friendly. The ease of integration with the CacheFlow appliance was yet another positive feature of Cyfin. We're now recommending it to our clients."
–Senior Analyst, Accenture, Chicago
"I am pleased to tell you we are happy with Cyfin Reporter. It is a revealing tool for our Internet usage report requirements. We use the Novell BorderManager proxy here with a filtering program to help enforce our strict Internet usage policy. The reports generated by Cyfin provide an excellent cross-check of the performance of our filtering software. Cyfin additionally provides well-formatted reports that upper management appreciates."
–Gary McHugh, Network Engineer, El Paso Electric Company
"I tested at least a dozen products before being introduced to Cyfin; I spent a lot of time working with other vendors' Sales and Support staff trying to make their systems do what Wescast required. I can honestly say that all the vendors tried their best to assist me but sometimes you cannot make systems do something they were not meant to do. I wish I had known about the Cyfin product from the start, the description alone would have steered me towards it first and I could have saved a lot of time.
I can honestly say there are a lot of great products available that claim they can provide Internet usage reports, but this is usually a bolt-on feature to a more robust system that provides reports on Web, FTP, firewall traffic, and so on. If you are really serious about monitoring Internet usage you need a product that focuses on this area. Cyfin is that product!
–Mick Montgomery, Wescast Industries Inc., Canada
"We are in the process of implementing Cyfin Reporter to provide our management with reports summarizing their staff's Internet usage.
The categorization of sites will help them to quickly review who is going where. Not having to try to decipher what a URL actually is, this is one of the positive features we see in this product. Having the ability to get granular detail on usage will provide us with the granular detail if needed."
–Richard Poworski, Saskatchewan Government Insurance, Canada
"We've found Cyfin to be very easy to install, configure and use. Its reports are clear, comprehensive and keep our managers closely informed with respect to our users' "outbound" Web activity patterns. This leads quickly to better decision-making, improved productivity, lower costs, and fewer personnel problems."
–Barbara A. Pettygrove, Blue Cross Blue Shield, Kansas
"Using the Cyfin reporting options, we created useful HTML reports on Web usage that can be viewed using most popular Web browsers. These reports can also be generated automatically and e-mailed to managers on a set schedule."
–Francis Chu, eWEEK Labs, San Francisco
"We have previously deployed eBorder and Cyfin and were pleased with the features and functionality of both products relating to how they operated independently of each other. Now that the products are integrated, we expect both applications to be more useful to NEC as we manage our global communication requirements."
–Hiroyuki Okada, General Manager of NEC's IT Strategy Division, responsible for global intranet operations, NEC, Singapore.
"We have been evaluating Cyfin for the past 20 days and found it to be an extremely good tool for understanding our internet traffic. The reports generated are fantastic and are very helpful."
–Ravi Kumar, Westbound Consulting Services, India
"When I downloaded your software I was so astonished about the features and the kind of reports I can get from it."
–Osama Al-Khiary, Alfaisaliah Group, Saudi Arabia
"Cyfin Reporter is a great tool to monitor Internet usage and quickly identify problem users."
–Ben Gillett, Beluga Ventures
"Working in a large IT organization I really needed to get a handle on our bandwidth usage broken down by department. After some evaluation we chose to forge ahead with Wavecrest and had the product implemented within a few days. As with all implementations we found a couple small issues that were most likely unique to our organization but had work-arounds and were not showstoppers. The product speaks for itself but what was amazing was the speed at which the Wavecrest support staff, including the developers, were able to quickly understand our issue, write a patch for it, and ensure that it was part of the next release of the product, eliminating our need for a work-around.
–Trent Leinenweber, IS/IT Manager, CGI Group
I believe there will be many benefits to using this product. One thing I noticed was the level of accuracy in the reporting. HR needs 100% confidence in the reports when a situation arises that requires any type of disciplinary action. The timeliness of the reports and quick generation of user audit reports will allow HR to deal with situations quickly. Wescast has a rule that states any abuse must be dealt with within 3 days of discovery for union employees."
–Mick Montgomery, Wescast Industries Inc., Canada
After the first month of running reports we were able to reduce bandwidth usage by 42% which we feel was a huge success, and the product’s ROI was less than 5 months by not having to increase bandwidth costs. The 42% bandwidth savings was obtained by a combination of a soft approach with members who now understand that all traffic can be easily reported on, as well as some desktop services that were pointing to the Internet for updates instead of local servers. Any IT managers that are looking to get a better handle on their bandwidth consumption I strongly recommend starting with Cyfin."
–Trent Leinenweber, IS/IT Manager, CGI Group
Our purchase of the Wavecrest Cyfin product was a success for us. We needed the ability to view, report and allow us to enforce all URL traffic from BOTH our Windows traffic as well as our MAC users traffic. The reporting is awesome. And I have to say the few times I’ve needed tech support, they are on it. I’ve been working in IT for over 20 years and have never had such headache free support. Their knowledge of the product is unsurpassed, and their near instant response is unheard of in todays environment. Anybody else, I cringe at the idea of making a tech support call, but with Cyfin, if you call or email you better be prepared to get an immediate response. And if it is too quick for you, scheduling for you convenience is not a problem. Hats off to tech support. Highly recommended product."
–System Administrator, Healthcare Industry
Why Us
- Industry Leader Since 1996 – Stability, Experience, and Knowledge.
- Global Customer Base – Customers on every continent except Antarctica.
- The Right Focus – Concentrating on The Human Factor.
- Best-of-Breed Products – Visibility, Compliance, Security, and Productivity.
- Exceptional Support – Dedicated, Effective, and Responsive Support.
- Best Value in Key Areas – Functionality, Price, Support, and Customer Service.









