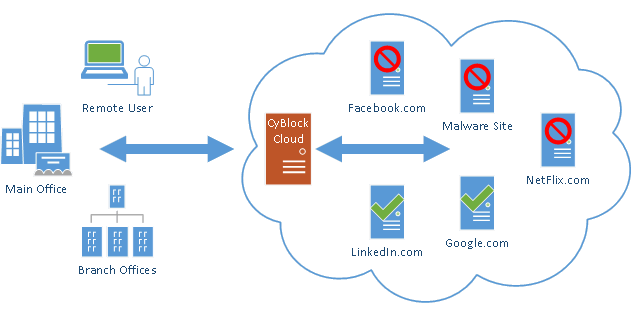
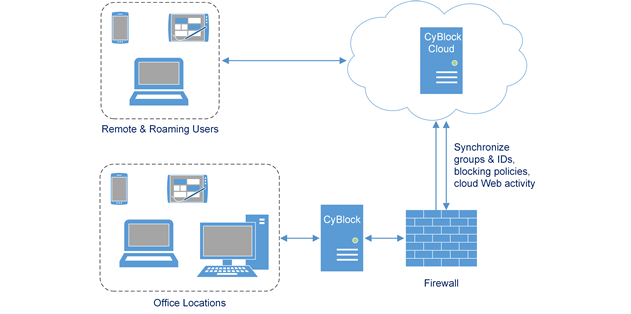
Advanced Employee Web Filtering and Monitoring Hybrid Deployment
Cover your distributed workforce with a local CyBlock install for office locations and CyBlock Cloud for remote and roaming users.
The CyBlock Hybrid Difference
Secure Web Content Filter
- Manage real-time Web traffic.
- Optimized SSL Inspection.
- Limit employees' time online.
- Restrict or allow certain sites.
Virtual and Distributed Workforce
- Highly elastic and adaptable.
- Easily scale to all offices and users.
- Fits today’s distributed workforce.
- Perimeter-less Coverage.
Extensive Report Library
- Large library of prebuilt reports.
- Start using impactful reports instantly.
- Easily distribute ready-to-use reports.
- Quickly create custom reports.
- Dramatically reduce time to analyze.
Policy and Compliance Management
- Ensure the human factor is managed.
- Enforce Acceptable Use Policy.
- Verify compliance to CIPA & HIPAA.
- Continuous improvement process.
Hybrid Deployment Option
- Supports CyBlock hardware and virtual environments.
- Pair your local installation(s) of CyBlock with your cloud account.
- Extend employee Web filtering and monitoring to your entire distributed workforce.
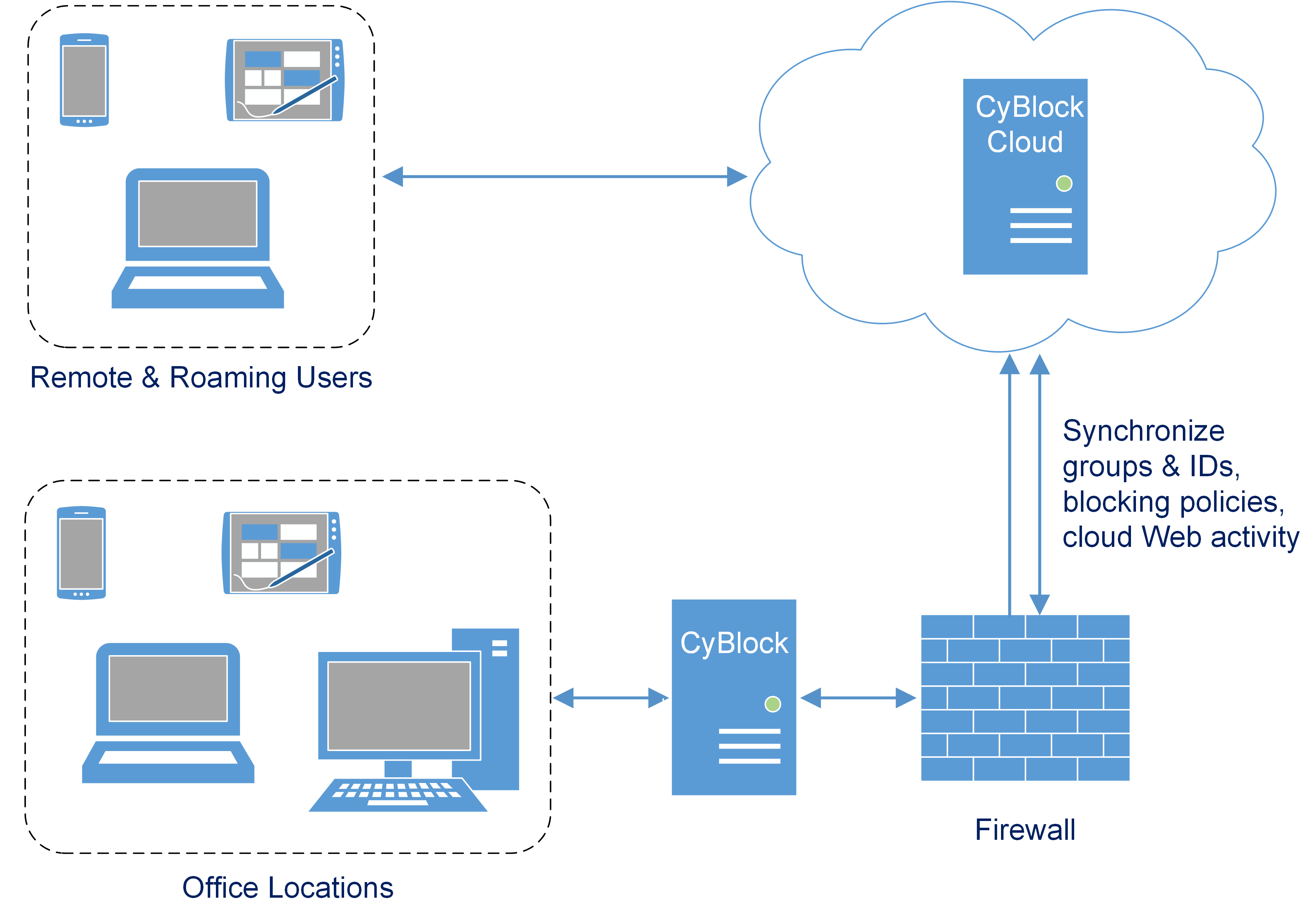
Advanced Filtering Scheduler
Advanced Filtering Features
- Apply a filtering schedule by day, hour, or half hour.
- Block general video streaming while allowing approved videos.
- Block prohibited search terms from being searched.
- Enable the Safe Search feature in all browsers.
- Fully inspect or “tunnel” secure Web traffic (HTTPS).
Web Content Filtering
- Filter based on the Website content category.
- Configure policy exceptions for different users and groups.
- Use white & black lists to restrict or allow access to certain sites.
- Enable users to bypass a blocking action with coaching.
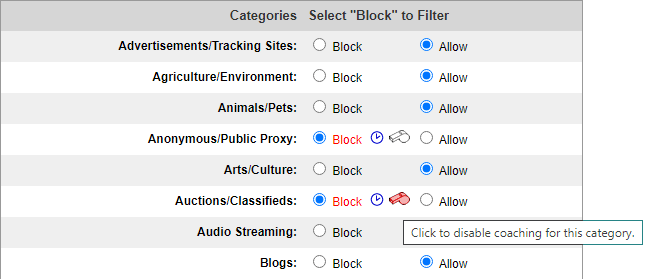
Web Content Filtering

Productivity & Time Online
Managing Productivity & Session Time Online
- Application and Website reports with session duration.
- Monitoring productivity and usage of company web services.
- Easily see how much time users are spending online.
- See session time by friendly Website name, not by ambiguous Domain Name.
- Accurately identify actual user clicks, providing managers with clear, useful data.
Additional Features & Exceptional Support: Quick Overview
- Advanced Proxy Filtering with Deep SSL Inspection.
- Comprehensive Web Monitoring, Logging & Reporting.
- Granular Web Access Control with Customizable Policies.
- U.S.-based expert technical support team.
- In-depth product knowledge for superior assistance.
- Committed to your success with comprehensive trial support.
Find the Right Cloud Deployment
Easy-to-launch cloud-based service applied regardless of employee location. Hosted and managed by Wavecrest, this option provides perimeter-less filtering and reporting coverage for all users - remote, roaming, flexible, and transitioning. Making this a popular choice for today’s distributed workforce environment.
Seamlessly integrate on-premises and cloud services for comprehensive web filtering and reporting. Ensure consistent policy enforcement for all users, whether they're onsite, remote, or on the move in hotels and airports.
Focused on simplicity and economy, our filtering-only solution is ideal for those who prioritize web security without the need for detailed reporting. Offering full cloud filtering capabilities, it's perfect for businesses with remote, roaming, or transitioning employees, providing proactive protection at an attractive price point.
Suggested Resources
Sign up for a custom CyBlock Hybrid Cloud demo.
Thank you! We will be in touch within one business day.
Once your request is processed, a product specialist will contact you to better understand your goals and schedule a custom product demo.
Why Us
- Industry Leader Since 1996 – Stability, Experience, and Knowledge.
- Global Customer Base – Customers on every continent except Antarctica.
- The Right Focus – Concentrating on The Human Factor.
- Best-of-Breed Products – Visibility, Compliance, Security, and Productivity.
- Exceptional Support – Dedicated, Effective, and Responsive Support.
- Best Value in Key Areas – Functionality, Price, Support, and Customer Service.