Advanced Filtering
Block Internet access with our RealTimePlus Internet filtering process.
- Block Web sites in 70+ different categories, e.g., Social Networking, Malware, and Updates/Downloads.
- Increase blocking coverage by filtering video, audio, images, etc. with our deep packet analysis.
- Customize real-time filtering by adding your own content types or URL extensions to be blocked.
- Use white lists to gain tighter control over which Web sites can be accessed.
- Greatly reduce your risk of security threats, e.g., malware and P2P/file sharing.
- Get enhanced protection by blocking public proxies, HTTPS, and cached pages.
- Easily create your own categories for additional site blocking and reporting.
- Enforce strict Safe Search mode for Google, Bing, and Yahoo!.
- Allow employees to surf normally blocked categories at specific times with half-hour blocking.
- Link to your organization's own blocking message or AUP to increase awareness of your Web-usage policy.
RealTimePlus Filtering – A Three-Layer Process
RealTimePlus is a customer-configurable three-layer filtering process. It uses three layers of screening based on: (1) custom categories, (2) the Wavecrest categorization (control) list, and (3) a real-time deep packet analysis process.
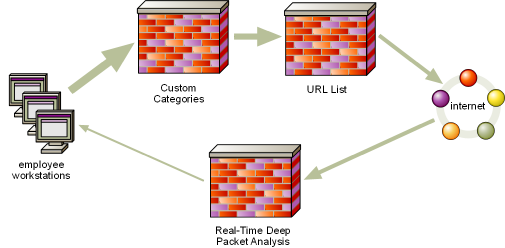
Users’ requests for visits must pass through all three layers to be allowed. If they don’t, access is denied.
The Three Layers
- Custom Categories (First Layer). Custom categories supplement the standard categories. This enables you to better identify and control your users’ Web activity. For example, you can create a custom category to:
- Serve as a white list that contains all sites to which visits are allowed (while blocking all others).
- Track and possibly block access to standard sites that are not in the Wavecrest URL List but are of special local interest or concern.
- Serve as a black list that contains all sites to be blocked (while allowing access to all others).
- Track visits to internal servers (intranet sites) and/or partner sites.
- The Wavecrest URL List (Second Layer). To accurately identify and categorize the vast majority of visits, Wavecrest products use a large, mature categorization control list. This control list consists of 70+ standard content-identification categories that Wavecrest populates and updates daily with URLs from around the world. Examples of standard categories include Shopping, News, Entertainment, Sports, Social Networking, Financial, and Pornography.
- Deep Packet Analysis (Third Layer). Using real-time deep packet analysis, the product can determine if the content of a URL is Flash, video streaming, audio streaming, images, Active X, and more. Any or all of these could be considered inappropriate. These can be blocked and customers can add their own extensions to be blocked.
Note: Wavecrest developed the list more than ten years ago and has continuously enlarged and improved it ever since. Moreover, the list is used in conjunction with a similarly mature and proven categorization process. Wavecrest updates and makes the list available on a daily basis. During initial product/policy setup, customers specify which users or groups of users should be denied access to which categories.
The Blocking Process
The blocking process works as follows:- Customers determine which types of traffic are inappropriate and thus prohibited.
- Users’ URL requests flow through all three layers.
- When a request matches any one of the prohibited types of traffic, the CyBlock product automatically blocks access to it.
- The product responds with a configurable blocking message. For example, it can be used to point to your own blocking policy.
Additional Information
Latency. An inline technique such as CyBlock’s RealTimePlus is the most effective way to filter Web use. However, by its very nature, an inline filter can introduce a certain amount of latency in performance. Wavecrest designed CyBlock with this potential in mind, and when the product is used in conjunction with our minimum recommended requirements for memory allocation and computer speed, the latency should be invisible.
© Copyright 1996-2025 Wavecrest Computing. All Rights Reserved.Thank you Wavecrest!"
-Chris Warren The Five Star Institute



