CyBlock Cloud - Effortless Integration With ConnectWise
CyBlock Cloud filtering service for MSPs provides ConnectWise integration for MSP Partners to easily manage licenses, analyze data, and protect customers from Web-borne threats.
The CyBlock Difference
Quick Launch Setup
- Deploy in minutes.
- No software to install.
- No hardware required.
- Simple, secure implementation.
Cloud-Based Web Filtering
- Always-on filtering.
- User/Group filter polices.
- Time based exceptions by day/hour.
- Block prohibited search terms.
Virtual and Distributed Workforce
- Highly elastic and adaptable.
- Easily scale to all offices and users.
- Fits today’s distributed workforce.
- Perimeter-less Coverage.
Save Money
- No need to purchase web gateway.
- Reduce required admin time for IT.
- Minimize infrastructure maintenance.
- Swift and continuous ROI.
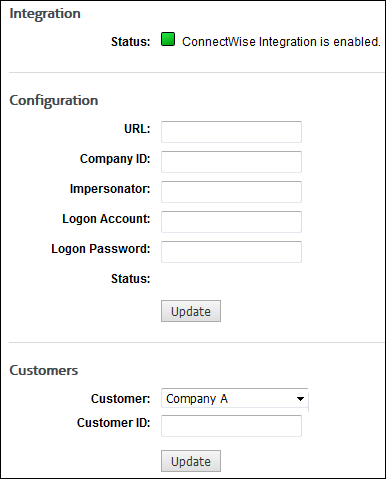
Set up ConnectWise Integration
Effortless Integration With ConnectWise
- Quick and easy setup for ConnectWise and CyBlock integration use.
- One click between ConnectWise and the CyBlock Cloud MSP Partner Portal.
- No need for additional software installation.
- Easily take advantage of ConnectWise service tickets and billing benefits.
Easily Track CyBlock Cloud Licenses
- CyBlock will automatically populate new information into the ConnectWise interface.
- Track & manage licenses, renewals, & more within your ConnectWise environment.
- Increase new and recurring revenue and customer satisfaction.
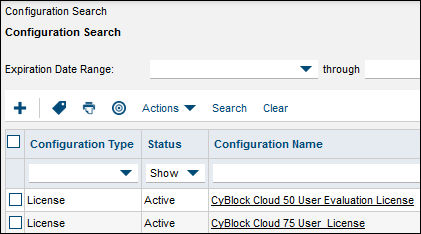
Track CyBlock Cloud Licenses
Advanced Filtering Scheduler
Advanced Filtering Features
- Apply a filtering schedule by day, hour, or half hour.
- Block general video streaming while allowing approved videos.
- Block prohibited search terms from being searched.
- Enable the Safe Search feature in all browsers.
- Fully inspect or “tunnel” secure Web traffic (HTTPS).
User Behavior Analytics
- Makes technical data easy to consume and manager-ready.
- Analyzes large volumes of data over long periods of time.
- Provides rapid and superior data insights.
- Tags associate related domains with friendly names.

Machine-Learning Behavior Analytics

Active Directory Integration
Active Directory Integration
- Seamless AD integration.
- Securely integrate AD Departments, Companies and Security Groups.
- Easily provide admin or manager access via AD integration.
- Limit manager access based their configured AD groups or departments.
CyBlock Complete Insight into Internet and Cloud Service Activity
Dashboard
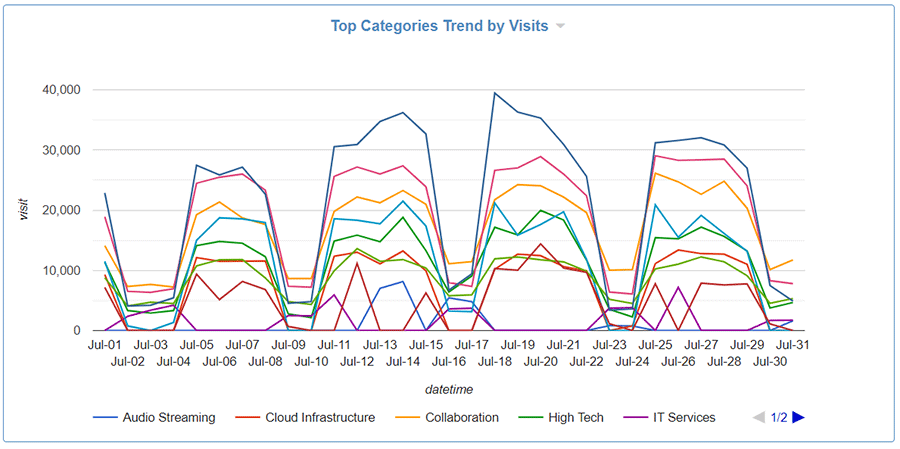
Top Categories Trend by Visits
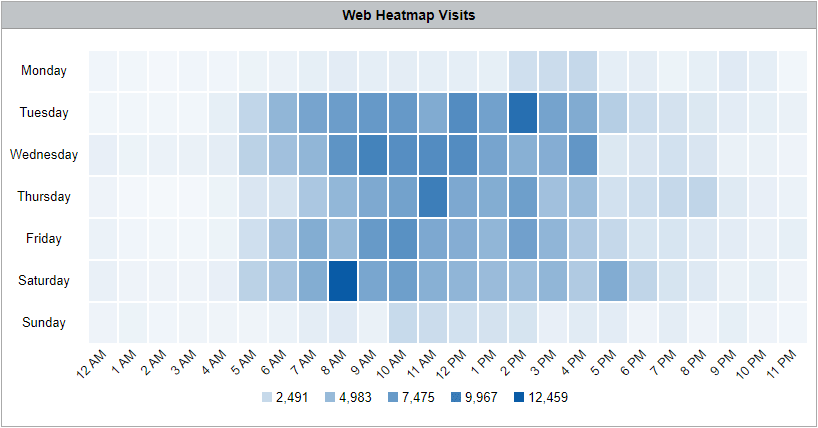
Heatmap - Web Visits by Hour
Trend - User Visit Activity
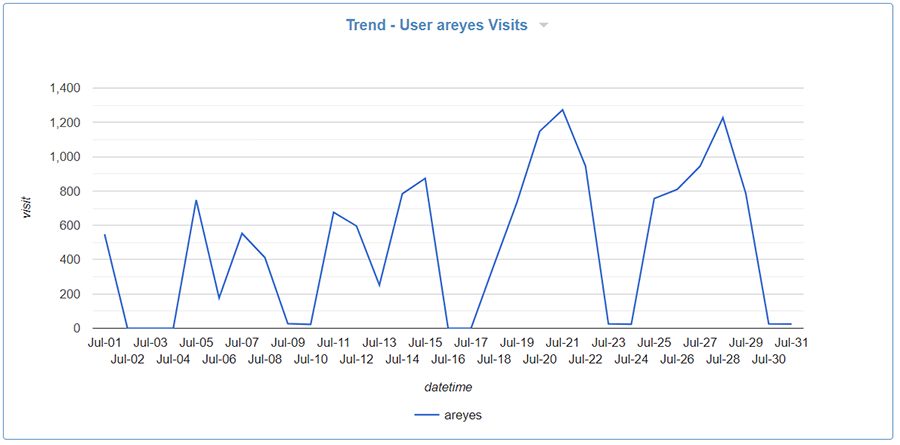
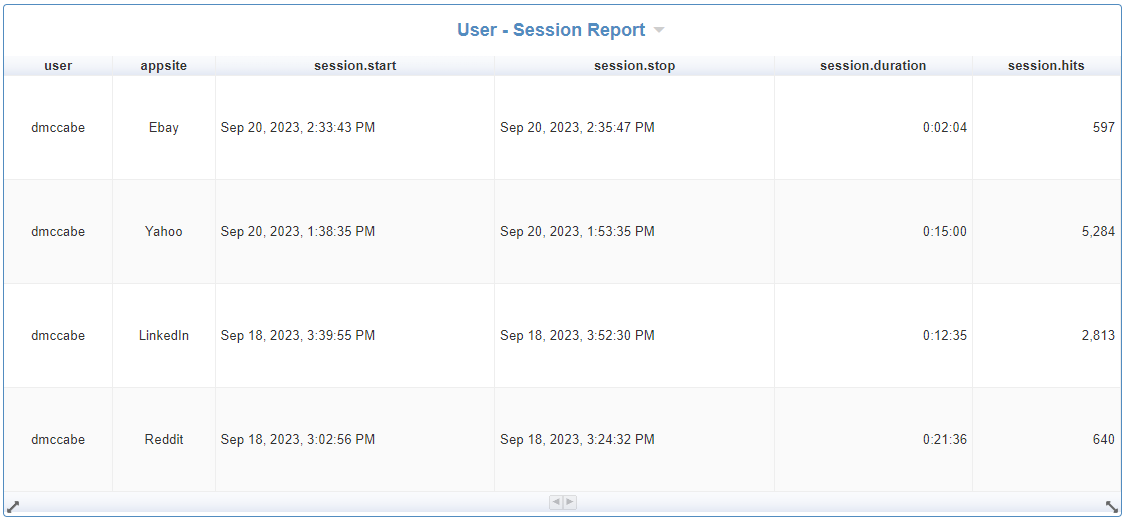
Table - User Session Audit Report
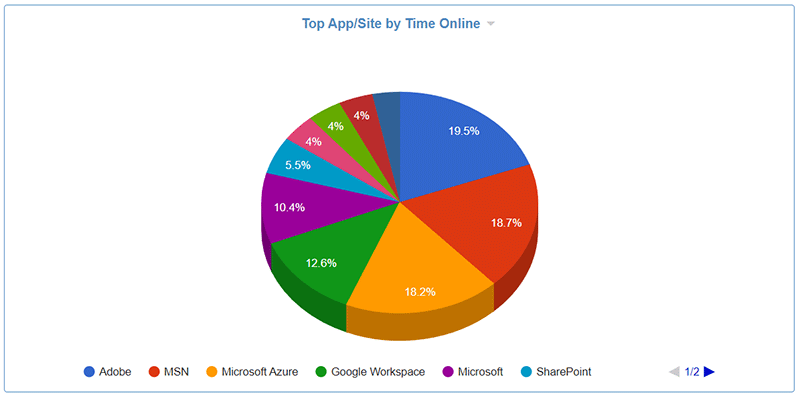
Pie Chart - Top App/Site by Time
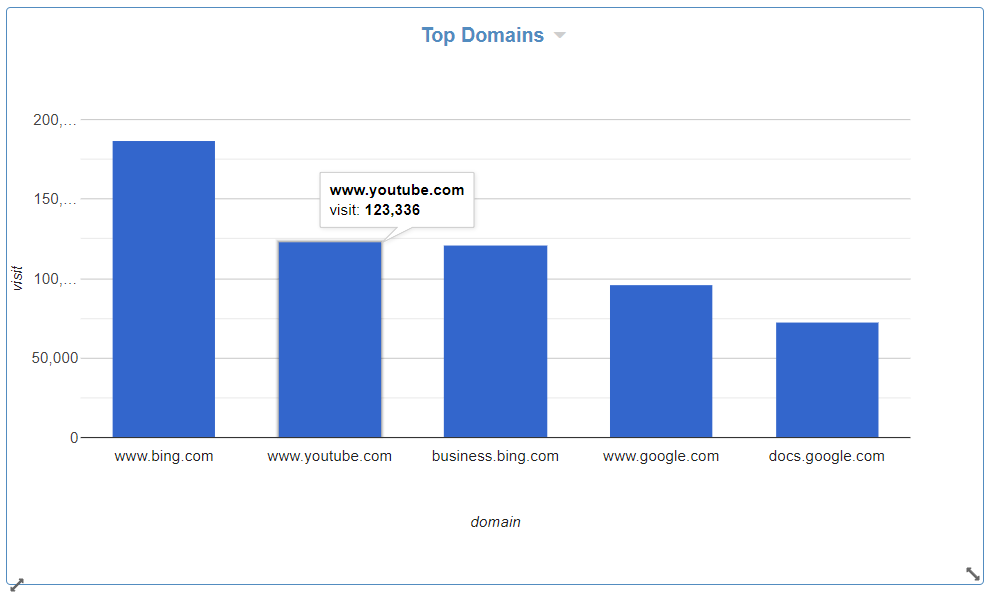
Top Chart - Domains by Visits
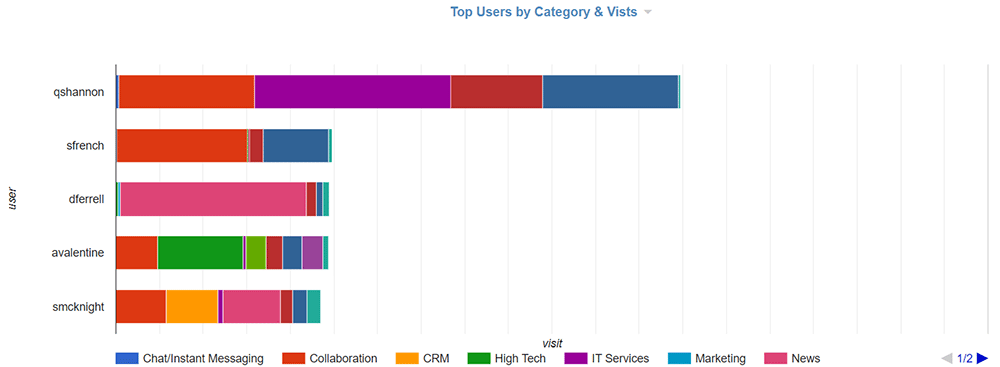
Top Chart - User by Category Visits
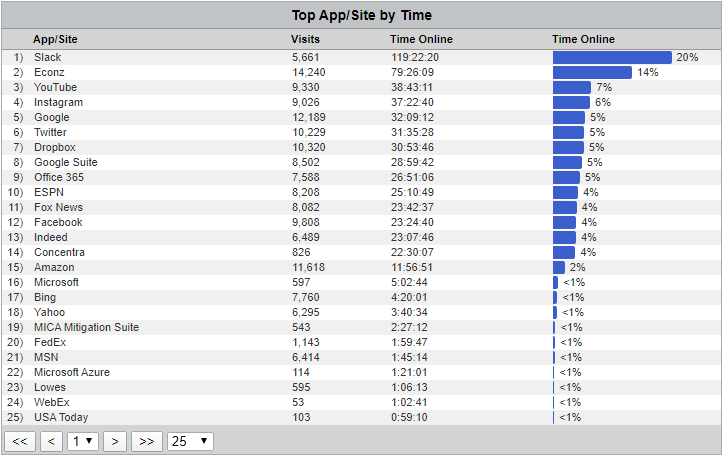
Top Table - App/Site by Time
Top Table - User by Time
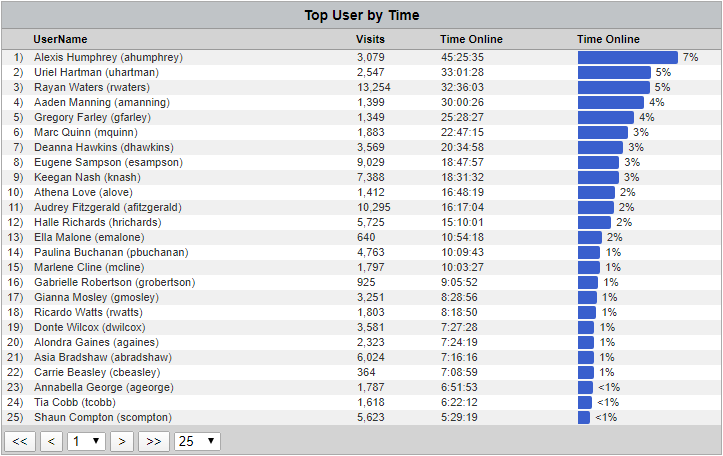
Table - User Audit Detail
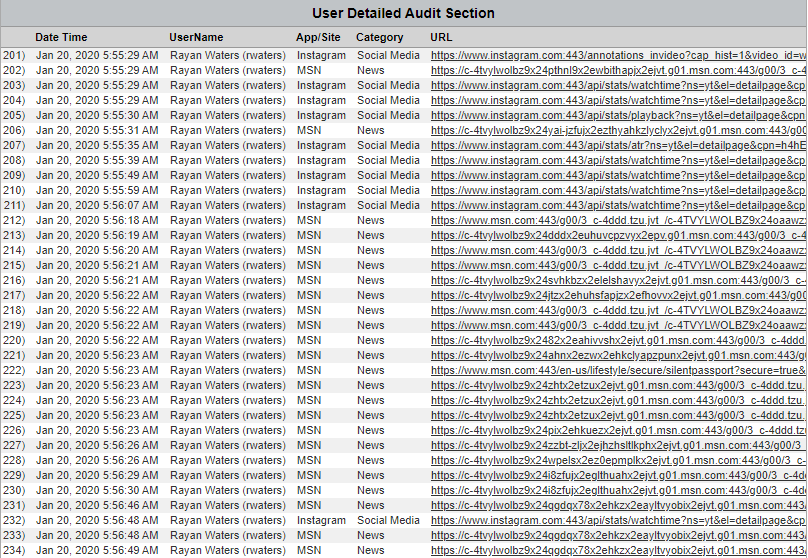
Table - App/Site Audit Detail
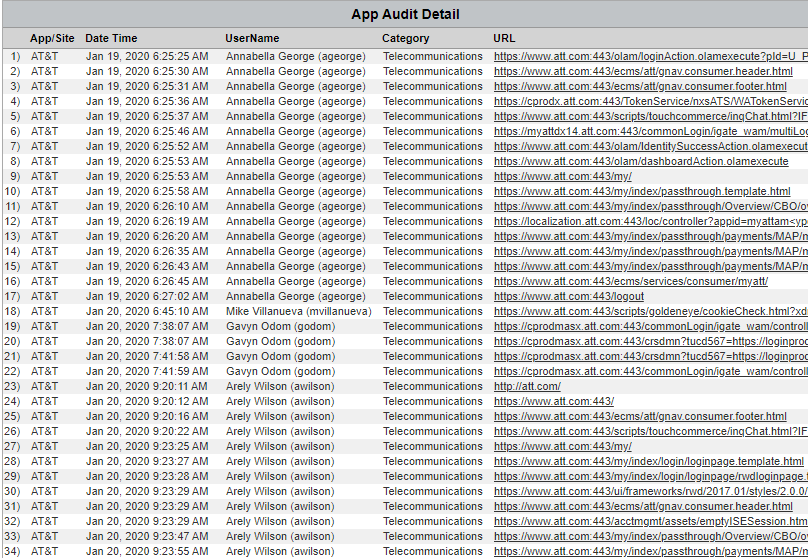
Table - Audit - Search Terms
Pie Chart - Microsoft 365 Top Users
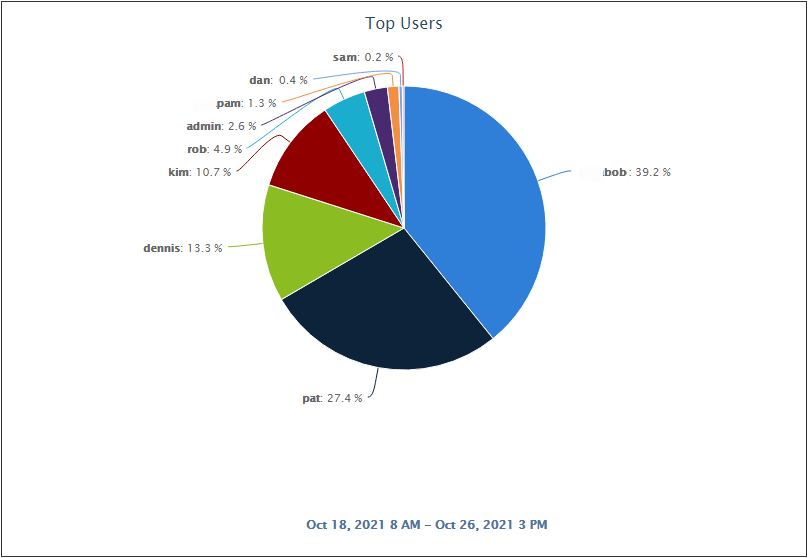
Top Chart - Microsoft 365 Top Operations
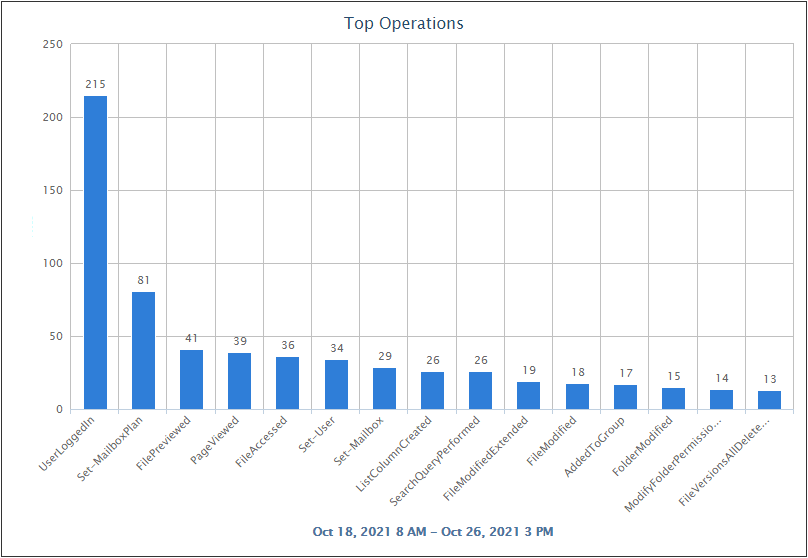
Table - Microsoft 365 OneDrive Audit
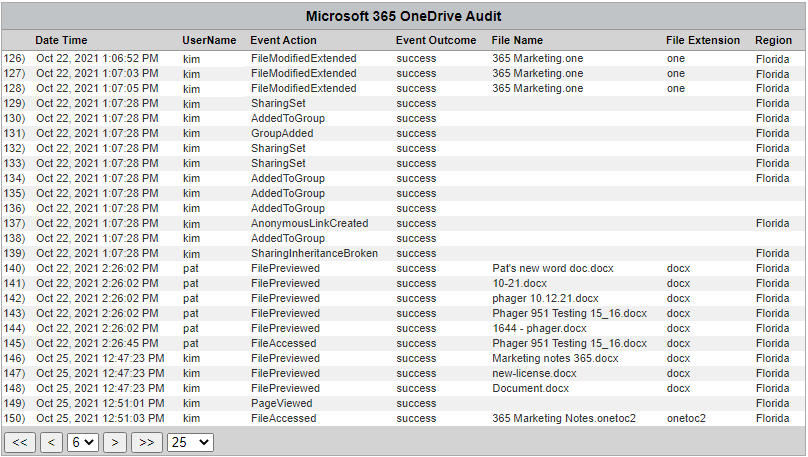
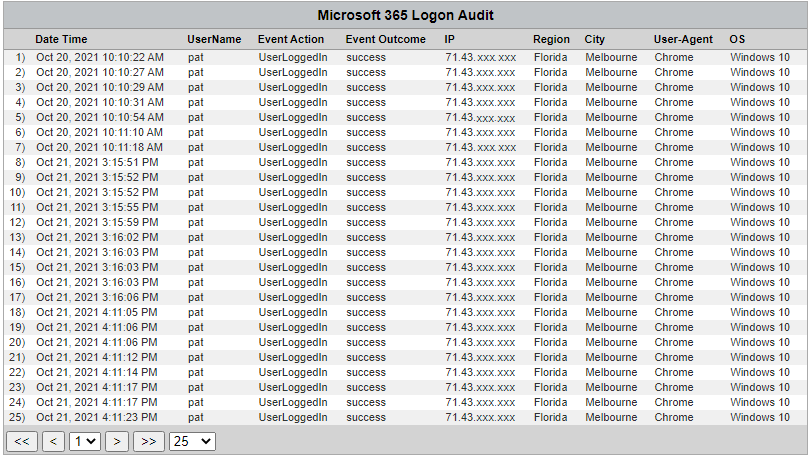
Table - Microsoft 365 User Logon Audit
Top VPN User Report
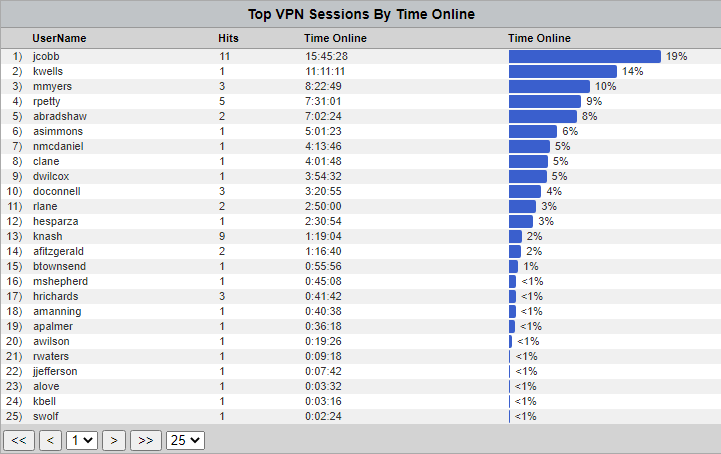
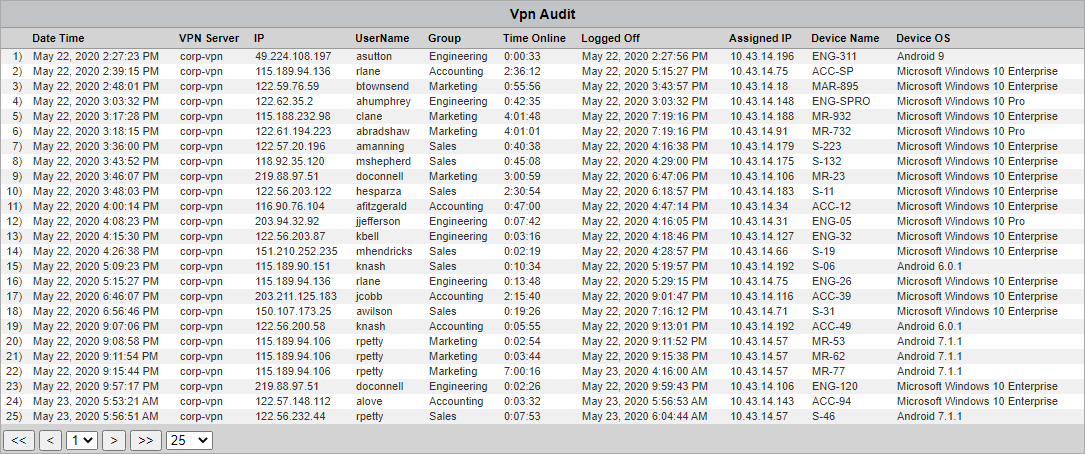
VPN User Audit Detail Report
Manage Employee Cloud Usage
- Discover all cloud applications being accessed in your organization.
- Expose both corporate-sanctioned and employee-introduced cloud services.
- Identify risk and analyze usage of your network resources.
- Meet security and compliance requirements while safely adopting cloud services.
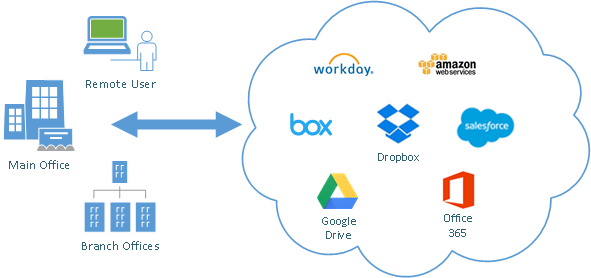
Manage Employee Cloud Usage

Advanced Threat Protection
Advanced Threat Protection
- Keep out malware, Trojan horses, spyware, phishing attacks, and more.
- Identify and stay ahead of a growing number of malware sites.
- Inspect or “tunnel” HTTPS by Web site, category, or user ID.
- Prevent crashes, slowdowns, and information theft.

Employee Web-Use Behavioral Analytics
- Expose abnormalities in user activity.
- Identify potential insider threat behavior.
- Flag possible legal liability issues.
- Assess trends for data breach exposure.
- Observe patterns for lost productivity.
Even More CyBlock Cloud Differences
Identify Human Action
- See actual Web browsing activity.
- All background clutter is removed.
- Determine user time online.
- User behavior analytics.
Policy and Compliance Management
- Ensure the human factor is managed.
- Enforce Acceptable Use Policy.
- Verify compliance to CIPA & HIPAA.
- Continuous improvement process.
Suggested Resources
Sign up for a custom CyBlock Cloud demo.
Thank you! We will be in touch within one business day.
Once your request is processed, a product specialist will contact you to better understand your goals and schedule a custom product demo.
What our customers are saying about CyBlock:
"I have been searching for years for a way to control internet access and to protect my users from hidden dangers, and Wavecrest CyBlock Cloud is the perfect solution. Installation was a breeze and support was fantastic. I highly recommend this product."
–Dave Baker, Johnstone Supply The Petit Group, LA
"CyBlock has helped my company improve productivity from our personnel by 60% since we implemented it's use within our network. This has been an invaluable tool that I'd recommend to anyone in need of filtering and blocking technology! Thank you Wavecrest"!
–Chris Warren The Five Star Institute
"CyBlock has for three years been a vital tool in our efforts to manage some 16,000 users' behaviour on the Web. Excellent functionality coupled with strong reporting capabilities has made our job much easier!"
–Jonas Sultan, AstraZeneca, Sweden
"We are pleased with the CyBlock product. We have been live with it for about 1 month now and find it to be useful for tracking our web usage. Yesterday I saw the activity light on our router flashing furiously so I ran an audit report and found out why by seeing which site(s) a couple of users were accessing."
–Phil Niles, Cottingham and Butler, Iowa
"Even though we have a full T1 at each location, I'd still say the benefit from more bandwidth is worth the cost of the software. I found out that one of my users downloaded a program that was hitting the Internet 9,000 times an hour. Needless to say that program has been removed."
–Roger Lewis, Northwest Bank and Trust, Iowa
Why Us
- Industry Leader Since 1996 – Stability, Experience, and Knowledge.
- Global Customer Base – Customers on every continent except Antarctica.
- The Right Focus – Concentrating on The Human Factor.
- Best-of-Breed Products – Visibility, Compliance, Security, and Productivity.
- Exceptional Support – Dedicated, Effective, and Responsive Support.
- Best Value in Key Areas – Functionality, Price, Support, and Customer Service.